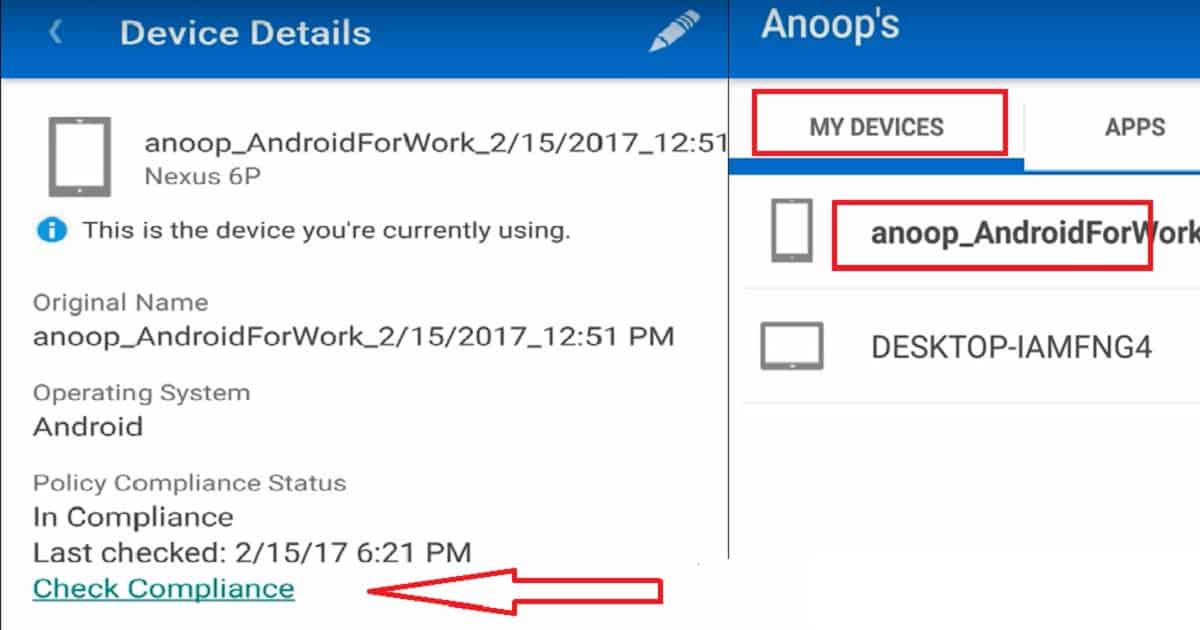
This section is for scripts that install or configure applications on the Mac. There are many reasons to deploy apps via shell script rather than via the macOS mdmclient. Our preferred method of app deployment is via the Mac App Store VPP, but the Intune Scripting agent provides an almost infinte level of possibilities where the apps you need. Samsung Smart Manager software, which ships on certain Samsung devices, can deactivate the Intune Company Portal and its components. When the Company Portal is in a deactivated state, it can't run in the background and can't contact the Intune service. Resolution 1: Tell your users to start the Company Portal app manually. Categories make it easier for users to find the app when they browse through the company portal. Show this as a featured app in the Company Portal: Display the app prominently on the main page of the company portal when users browse for apps. Information URL: Optionally, enter the URL of a website that contains information about this app. You can use Intune to query the status of disk encryption (File Vault II) on enrolled Mac devices and ensure that company data is encrypted at rest. Reporting and Auditing Intune helps you keep track of all your Mac devices by providing comprehensive hardware and software inventory reporting capabilities. You can go to the Reports workspace to. Adding the Citrix Workspace app as a line-of-business app in Microsoft Intune. Once the application has been created and assigned to users, it will be available for install in the Intune Company Portal. The application can also be set to required for automatic deployment. Citrix Workspace available in the Intune Company Portal on macOS.
- Microsoft Intune Company Portal
- Intune Company Portal Mac Download Software
- Intune Company Portal Mac Download Mac
This article provides suggestions for troubleshooting device enrollment issues. If this information doesn't solve your problem, see How to get support in Microsoft Endpoint Manager to find more ways to get help.
Initial troubleshooting steps
Before you begin troubleshooting, check to make sure that you've configured Intune properly to enable enrollment. You can read about those configuration requirements in:
- Set up Android device management - No additional steps required
You can also make sure that the time and date on the user's device are set correctly:
- Restart the device.
- Make sure that the time and date are set close to GMT standards (+ or - 12 hours) for the end user's time zone.
- Uninstall and reinstall the Intune company portal (if applicable).
Your managed device users can collect enrollment and diagnostic logs for you to review. User instructions for collecting logs are provided in:
General enrollment issues
These issues may occur on all device platforms.
Device cap reached
Issue: A user receives an error during enrollment (like Company Portal Temporarily Unavailable).
Resolution:
Check number of devices enrolled and allowed
Check to see that the user isn't assigned more than the maximum number of devices by following these steps:
In the Microsoft Endpoint Manager admin center, choose Devices > Enrollment restrictions > Device limit restrictions. Note the value in the Device limit column.
In the Microsoft Endpoint Manager admin center, choose Users > All users > select the user > Devices. Note the number of devices.
If the user's number of enrolled devices already equals their device limit restriction, they can't enroll anymore until:
- Existing devices are removed, or
- You increase the device limit by setting device restrictions.
To avoid hitting device caps, be sure to remove stale device records.
Note
You can avoid the device enrollment cap by using Device Enrollment Manager account, as described in Enroll corporate-owned devices with the Device Enrollment Manager in Microsoft Intune.
A user account that is added to Device Enrollment Managers account will not be able to complete enrollment when Conditional Access policy is enforced for that specific user login.
Company Portal Temporarily Unavailable
Issue: Users receive a Company Portal Temporarily Unavailable error on their device.
Resolution:
Remove the Intune Company Portal app from the device.
On the device, open the browser, browse to https://portal.manage.microsoft.com, and try a user login.
If the user fails to sign in, they should try another network.
If that fails, validate that the user's credentials have synced correctly with Azure Active Directory.
If the user successfully logs in, an iOS/iPadOS device will prompt you to install the Intune Company Portal app and enroll. On an Android device, you'll need to manually install the Intune Company Portal app, after which you can retry enrolling.
MDM authority not defined
Issue: A user receives an MDM authority not defined error.
Resolution:
Verify that the MDM Authority has been set appropriately.
Verify that the user's credentials have synced correctly with Azure Active Directory. You can verify that the user's UPN matches the Active Directory information in the Microsoft 365 admin center.If the UPN doesn't match the Active Directory information:
Turn off DirSync on the local server.
Delete the mismatched user from the Intune Account Portal user list.
Wait about one hour to allow the Azure service to remove the incorrect data.
Turn on DirSync again and check if the user is now synced properly.
Unable to create policy or enroll devices if the company name contains special characters
Issue: You can't create policy or enroll devices.
Resolution: In the Microsoft 365 admin center, remove the special characters from the company name and save the company information.
Unable to sign in or enroll devices when you have multiple verified domains
Issue: This problem may occur when you add a second verified domain to your AD FS. Users with the user principal name (UPN) suffix of the second domain may not be able to log into the portals or enroll devices.
Resolution: Microsoft 365 customers are required to deploy a separate instance of the AD FS 2.0 Federation Service for each suffix if they:
- use single sign-on (SSO) through AD FS 2.0, and
- have multiple top-level domains for users' UPN suffixes within their organization (for example, @contoso.com or @fabrikam.com).
A rollup for AD FS 2.0 works in conjunction with the SupportMultipleDomain switch to enable the AD FS server to support this scenario without requiring additional AD FS 2.0 servers. For more information, see this blog.
Android issues
Android enrollment errors
The following table lists errors that end users might see while enrolling Android devices in Intune.
| Error message | Issue | Resolution |
|---|---|---|
| IT admin needs to assign license for access Your IT admin hasn't given you access to use this app. Get help from your IT admin or try again later. | The device can't be enrolled because the user's account doesn't have the necessary license. | Before users can enroll their devices, they must have been assigned the necessary license. This message means that they have the wrong license type for the mobile device management authority. For example, they'll see this error if both of the following are true:
|
| IT admin needs to set MDM authority Looks like your IT admin hasn't set an MDM authority. Get help from your IT admin or try again later. | The mobile device management authority hasn't been defined. | The mobile device management authority hasn't been set in Intune. See information about how to set the mobile device management authority. |
Devices fail to check in with the Intune service and display as Unhealthy in the Intune admin console
Issue: Some Samsung devices that are running Android versions 4.4.x and 5.x might stop checking in with the Intune service. If devices don't check in:
- They can't receive policy, apps, and remote commands from the Intune service.
- They show a Management State of Unhealthy in the administrator console.
- Users who are protected by Conditional Access policies might lose access to corporate resources.
Samsung Smart Manager software, which ships on certain Samsung devices, can deactivate the Intune Company Portal and its components. When the Company Portal is in a deactivated state, it can't run in the background and can't contact the Intune service.
Resolution 1:
Tell your users to start the Company Portal app manually. Once the app restarts, the device checks in with the Intune service.
Important
Opening the Company Portal app manually is a temporary solution, because Samsung Smart Manager may deactivate the Company Portal app again.
Resolution 2:
Tell your users to try upgrading to Android 6.0. The deactivation issue doesn't occur on Android 6.0 devices. To check if an update is available, go to Settings > About device > Download updates manually > follow the prompts.
Resolution 3:
If Resolution 2 doesn't work, have your users follow these steps to make Smart Manager exclude the Company Portal app:
Launch the Smart Manager app on the device.
Choose the Battery tile.
Under App power saving or App optimization, select Detail.
Choose Company Portal from the list of apps.
Choose Turned off.
Under App power saving or App optimization, confirm that Company Portal is turned off.
Profile installation failed
Issue: A user receives a Profile installation failed error on an Android device.
Resolution:
Confirm that the user is assigned an appropriate license for the version of the Intune service that you're using.
Confirm that the device isn't already enrolled with another MDM provider.
Confirm that the device doesn't already have a management profile installed.
Confirm that Chrome for Android is the default browser and that cookies are enabled.
Android certificate issues
Issue: Users receive the following message on their device:You can't sign in because your device is missing a required certificate.
Resolution 1:
The user might be able to retrieve the missing certificate by following the instructions in Your device is missing a required certificate. If the error persists, try Resolution 2.
Resolution 2:
After entering their corporate credentials and getting redirected for federated login, users might still see the missing certificate error. In this case, the error may mean that an intermediate certificate is missing from your Active Directory Federation Services (AD FS) server
The certificate error occurs because Android devices require intermediate certificates to be included in an SSL Server hello. Currently, a default AD FS server or WAP - AD FS Proxy server installation sends only the AD FS service SSL certificate in the SSL server hello response to an SSL Client hello.
To fix the issue, import the certificates into the Computers Personal Certificates on the AD FS server or proxies as follows:
- On the AD FS and proxy servers, right-click Start > Run > certlm.msc to launch the Local Machine Certificate Management Console.
- Expand Personal and choose Certificates.
- Find the certificate for your AD FS service communication (a publicly signed certificate), and double-click to view its properties.
- Choose the Certification Path tab to see the certificate's parent certificate/s.
- On each parent certificate, choose View Certificate.
- Choose Details > Copy to file….
- Follow the wizard prompts to export or save the public key of the parent certificate to the file location of your choice.
- Right-click Certificates > All Tasks > Import.
- Follow the wizard prompts to import the parent certificate(s) to Local ComputerPersonalCertificates.
- Restart the AD FS servers.
- Repeat the above steps on all of your AD FS and proxy servers.
To verify a proper certificate installation, you can use the diagnostics tool available on https://www.digicert.com/help/. In the Server Address box, enter your AD FS server's FQDN, such as sts.contoso.com, and then click Check Server.
To validate that the certificate installed correctly:
The follow steps describe just one of many methods and tools that you can use to validate that the certificate installed correctly.
- Go to the free Digicert tool.
- Enter your AD FS server's fully qualified domain name (for example, sts.contoso.com) and select CHECK SERVER.
If the Server certificate is installed correctly, you see all check marks in the results. If the problem above exists, you see a red X in the Certificate Name Matches and the SSL Certificate is correctly Installed sections of the report.
Resolution 3:
The users are unable to authenticate in Company Portal. But they can authenticate in Microsoft Authenticator and web browsers.
This issue occurs if your AD FS server uses a user certificate rather than a certificate issued by a public certificate authority (CA).
There are two certificate stores in Android devices:
- The user certificate store
- The system certificate store
Staring in Android 7.0, apps ignore user certificates by default, unless the apps explicitly opt in. For more information, see Changes to Trusted Certificate Authorities in Android Nougat.
To fix this issue, use a certificate that chains to a publicly trusted root CA in your AD FS server. A list of public CAs on Android can be found at https://android.googlesource.com/platform/system/ca-certificates/+/master/files/.
iOS/iPadOS issues
iOS/iPadOS enrollment errors
The following table lists errors that end users might see while enrolling iOS/iPadOS devices in Intune.
| Error message | Issue | Resolution |
|---|---|---|
| NoEnrollmentPolicy | No enrollment policy found | Check that all enrollment prerequisites, like the Apple Push Notification Service (APNs) certificate, have been set up and that iOS/iPadOS as a platform is enabled. For instructions, see Set up iOS/iPadOS and Mac device management. |
| DeviceCapReached | Too many mobile devices are enrolled already. | The user must remove one of their currently enrolled mobile devices from the Company Portal before enrolling another. See the instructions for the type of device you're using: Android, iOS/iPadOS, Windows. |
| APNSCertificateNotValid | There's a problem with the certificate that lets the mobile device communicate with your company's network. | The Apple Push Notification Service (APNs) provides a channel to contact enrolled iOS/iPadOS devices. Enrollment will fail and this message will appear if:
|
| AccountNotOnboarded | There's a problem with the certificate that lets the mobile device communicate with your company's network. | The Apple Push Notification Service (APNs) provides a channel to contact enrolled iOS/iPadOS devices. Enrollment will fail and this message will appear if:
|
| DeviceTypeNotSupported | The user might have tried to enroll using a non-iOS device. The mobile device type that you're trying to enroll isn't supported. Confirm that device is running iOS/iPadOS version 8.0 or later. | Make sure that your user's device is running iOS/iPadOS version 8.0 or later. |
| UserLicenseTypeInvalid | The device can't be enrolled because the user's account isn't yet a member of a required user group. | Before users can enroll their devices, they must be members of the right user group. This message means that they have the wrong license type for the mobile device management authority. For example, they'll see this error if both of the following are true:
Review Set up iOS/iPadOS and Mac management with Microsoft Intune and information about how to set up users in Sync Active Directory and add users to Intune and organizing users and devices. |
| MdmAuthorityNotDefined | The mobile device management authority hasn't been defined. | The mobile device management authority hasn't been set in Intune. Review item #1 in the Step 6: Enroll mobile devices and install an app section in Get started with a 30-day trial of Microsoft Intune. |
Devices are inactive or the admin console can't communicate with them
Issue: iOS/iPadOS devices aren't checking in with the Intune service. Devices must check in periodically with the service to maintain access to protected corporate resources. If devices don't check in:
- They can't receive policy, apps, and remote commands from the Intune service.
- They show a Management State of Unhealthy in the administrator console.
- Users who are protected by Conditional Access policies might lose access to corporate resources.
Resolution: Share the following resolutions with your end users to help them regain access to corporate resources.
When users start the iOS/iPadOS Company Portal app, it can tell if their device has lost contact with Intune. If it detects that there's no contact, it automatically tries to sync with Intune to reconnect (users will see the Trying to sync… message).
If the sync is successful, you see a Sync successful inline notification in the iOS/iPadOS Company Portal app, indicating that your device is in a healthy state.
If the sync is unsuccessful, users see an Unable to sync inline notification in the iOS/iPadOS Company Portal app.
To fix the issue, users must select the Set up button, which is to the right of the Unable to sync notification. The Set up button takes users to the Company Access Setup flow screen, where they can follow the prompts to enroll their device.
Once enrolled, the devices return to a healthy state and regain access to company resources.
Verify WS-Trust 1.3 is enabled
Issue Automated Device Enrollment (ADE) iOS/iPadOS devices can't be enrolled
Enrolling ADE devices with user affinity requires WS-Trust 1.3 Username/Mixed endpoint to be enabled to request user tokens. Active Directory enables this endpoint by default. To get a list of enabled endpoints, use the Get-AdfsEndpoint PowerShell cmdlet and looking for the trust/13/UsernameMixed endpoint. For example:
For more information, see Get-AdfsEndpoint documentation.
For more information, see Best practices for securing Active Directory Federation Services. For help with determining if WS-Trust 1.3 Username/Mixed is enabled in your identity federation provider:
- contact Microsoft Support if you use AD FS
- contact your third-party identity vendor.
Profile installation failed
Issue: A user receives a Profile installation failed error on an iOS/iPadOS device.
Troubleshooting steps for failed profile installation
Confirm that the user is assigned an appropriate license for the version of the Intune service that you're using.
Confirm that the device isn't already enrolled with another MDM provider.
Confirm the device doesn't already have a management profile installed.
Navigate to https://portal.manage.microsoft.com and try to install the profile when prompted.
Confirm that Safari for iOS/iPadOS is the default browser and that cookies are enabled.
User's iOS/iPadOS device is stuck on an enrollment screen for more than 10 minutes
Issue: An enrolling device may get stuck in either of two screens:
- Awaiting final configuration from 'Microsoft'
- Guided Access app unavailable. Please contact your administrator.
This issue can happen if:
- there's a temporary outage with Apple services, or
- iOS/iPadOS enrollment is set to use VPP tokens as shown in the table but there's something wrong with the VPP token.
| Enrollment settings | Value |
|---|---|
| Platform | iOS/iPadOS |
| User Affinity | Enroll with User Affinity |
| Authenticate with Company Portal instead of Apple Setup Assistant | Yes |
| Install Company Portal with VPP | Use token: token address |
| Run Company Portal in Single App Mode until authentication | Yes |
Resolution: To fix the problem, you must:
- Determine if there's something wrong with the VPP token and fix it.
- Identify which devices are blocked.
- Wipe the affected devices.
- Tell the user to restart the enrollment process.
Determine if there's something wrong with the VPP token
- In the Microsoft Endpoint Manager admin center, choose Devices > iOS/iPadOS > iOS enrollment > Enrollment program tokens > token name > Profiles > profile name > Manage > Properties.
- Review the properties to see if any errors similar to the following appear:
- This token has expired.
- This token is out of Company Portal licenses.
- This token is being used by another service.
- This token is being used by another tenant.
- This token was deleted.
- Fix the issues for the token.
Identify which devices are blocked by the VPP token
- In the Microsoft Endpoint Manager admin center, choose Devices > iOS/iPadOSk > iOS enrollment > Enrollment program tokens > token name > Devices.
- Filter the Profile status column by Blocked.
- Make a note of the serial numbers for all the devices that are Blocked.
Remotely wipe the blocked devices
After you've fixed the issues with the VPP token, you must wipe the devices that are blocked.
- In the Microsoft Endpoint Manager admin center, choose Devices > All devices > Columns > Serial number > Apply.
- For each blocked device, choose it in the All devices list and then choose Wipe > Yes.
Tell the users to restart the enrollment process
After you've wiped the blocked devices, you can tell the users to restart the enrollment process.
macOS issues
macOS enrollment errors
Error message 1:It looks like you're using a virtual machine. Make sure you've fully configured your virtual machine, including serial number and hardware model. If this isn't a virtual machine, please contact support.
Error message 2:We're having trouble getting your device managed. This problem could be caused if you're using a virtual machine, have a restricted serial number, or if this device is already assigned to someone else. Learn how to resolve these problems or contact your company support.
Issue: This message could be a result of any of the following reasons:
- A macOS virtual machine (VM) isn't configured correctly
- You've enabled device restrictions that require the device to be corporate-owned or have a registered device serial number in Intune
- The device has already been enrolled and is still assigned to someone else in Intune
Resolution: First, check with your user to determine which of the issues affects their device. Then complete the most relevant of the following solutions:
If the user is enrolling a VM for testing, make sure it's been fully configured so that Intune can recognize its serial number and hardware model. Learn more about how to set up VMs in Intune.
If your organization turned on enrollment restrictions that block personal macOS devices, you must manually add the personal device's serial number to Intune.
If the device is still assigned to another user in Intune, its former owner did not use the Company Portal app to remove or reset it. To clean up the stale device record from Intune:
- In the Microsoft Endpoint Manager admin center, sign in with your administrative credentials.
- Choose Devices > All devices.
- Find the device with the enrollment problem. Search by device name or MAC/HW Address to narrow your results.
- Select the device > Delete. Delete all other entries associated with the device.
PC Issues
| Error message | Issue | Resolution |
|---|---|---|
| IT admin needs to assign license for access Your IT admin hasn't given you access to use this app. Get help from your IT admin or try again later. | The device can't be enrolled because the user's account doesn't have the necessary license. | Before users can enroll their devices, they must have been assigned the necessary license. This message means that they have the wrong license type for the mobile device management authority. For example, they'll see this error if both of the following are true:
|
The machine is already enrolled - Error hr 0x8007064c
Issue: Enrollment fails with the error The machine is already enrolled. The enrollment log shows error hr 0x8007064c.
This failure may occur because the computer:
- was previously enrolled, or
- has the cloned image of a computer that was already enrolled.The account certificate of the previous account is still present on the computer.
Resolution:
From the Start menu, type Run -> MMC.
Choose File > Add/ Remove Snap-ins.
Double-click Certificates, choose Computer account > Next, and select Local Computer.
Double-click Certificates (Local computer) and choose Personal/ Certificates.
Look for the Intune cert issued by Sc_Online_Issuing, and delete it, if present.
If the following registry key exists, delete it: HKEY_LOCAL_MACHINESOFTWAREMicrosoftOnlineManagement regkey and all sub keys.
Try to re-enroll.
If the PC still can't enroll, look for and delete this key, if it exists: KEY_CLASSES_ROOTInstallerProducts6985F0077D3EEB44AB6849B5D7913E95.
Try to re-enroll.
Important
This section, method, or task contains steps that tell you how to modify the registry. However, serious problems might occur if you modify the registry incorrectly. Therefore, make sure that you follow these steps carefully. For added protection, back up the registry before you modify it. Then, you can restore the registry if a problem occurs.For more information about how to back up and restore the registry, read How to back up and restore the registry in Windows
General enrollment Error codes
| Error code | Possible problem | Suggested resolution |
|---|---|---|
| 0x80CF0437 | The clock on the client computer isn't set to the correct time. | Make sure that the clock and the time zone on the client computer are set to the correct time and time zone. |
| 0x80240438, 0x80CF0438, 0x80CF402C | can't connect to the Intune service. Check the client proxy settings. | Verify that Intune supports the proxy configuration on the client computer. Verify that the client computer has Internet access. |
| 0x80240438, 0x80CF0438 | Proxy settings in Internet Explorer and Local System aren't configured. | can't connect to the Intune service. Check the client proxy settings. Verify that Intune supports the proxy configuration on the client computer. Verify that the client computer has Internet access. |
| 0x80043001, 0x80CF3001, 0x80043004, 0x80CF3004 | Enrollment package is out of date. | Download and install the current client software package from the Administration workspace. |
| 0x80043002, 0x80CF3002 | Account is in maintenance mode. | You can't enroll new client computers when the account is in maintenance mode. To view your account settings, sign in to your account. |
| 0x80043003, 0x80CF3003 | Account is deleted. | Verify that your account and subscription to Intune is still active. To view your account settings, sign in to your account. |
| 0x80043005, 0x80CF3005 | The client computer has been retired. | Wait a few hours, remove any older versions of the client software from the computer, and then retry the client software installation. |
| 0x80043006, 0x80CF3006 | The maximum number of seats allowed for the account has been reached. | Your organization must buy additional seats before you can enroll more client computers in the service. |
| 0x80043007, 0x80CF3007 | Couldn't find the certificate file in the same folder as the installer program. | Extract all files before you start the installation. Do not rename or move any of the extracted files: all files must exist in the same folder or the installation will fail. |
| 0x8024D015, 0x00240005, 0x80070BC2, 0x80070BC9, 0x80CFD015 | The software can't be installed because a restart of the client computer is pending. | Restart the computer and then retry the client software installation. |
| 0x80070032 | One or more prerequisites for installing the client software weren't found on the client computer. | Make sure that all required updates are installed on the client computer and then retry the client software installation. |
| 0x80043008, 0x80CF3008 | Failed to start the Microsoft Online Management Updates service. | Contact Microsoft Support as described in How to get support in Microsoft Endpoint Manager. |
| 0x80043009, 0x80CF3009 | The client computer is already enrolled into the service. | You must retire the client computer before you can re-enroll it in the service. |
| 0x8004300B, 0x80CF300B | The client software installation package can't run because the version of Windows that is running on the client isn't supported. | Intune doesn't support the version of Windows that is running on the client computer. |
| 0xAB2 | The Windows Installer couldn't access VBScript run time for a custom action. | This error is caused by a custom action that is based on Dynamic-Link Libraries (DLLs). |
| 0x80cf0440 | The connection to the service endpoint terminated. | Trial or paid account is suspended. Create a new trial or paid account and re-enroll. |
Next steps
If this troubleshooting information didn't help you, contact Microsoft Support as described in How to get support in Microsoft Endpoint Manager.
-->Use the information in this article to help you add macOS line-of-business apps to Microsoft Intune. You must download an external tool to pre-process your .pkg files before you can upload your line-of-business file to Microsoft Intune. The pre-processing of your .pkg files must take place on a macOS device.
Note
Starting with the release of macOS Catalina 10.15, prior to adding your apps to Intune, check to make sure your macOS LOB apps are notarized. If the developers of your LOB apps did not notarize their apps, the apps will fail to run on your users' macOS devices. For more information about how to check if an app is notarized, visit Notarize your macOS apps to prepare for macOS Catalina.
Note
While users of macOS devices can remove some of the built-in macOS apps like Stocks, and Maps, you cannot use Intune to redeploy those apps. If end users delete these apps, they must go to the app store, and manually re install them.
Before your start
You must download an external tool, mark the downloaded tool as an executable, and pre-process your .pkg files with the tool before you can upload your line-of-business file to Microsoft Intune. The pre-processing of your .pkg files must take place on a macOS device. Use the Intune App Wrapping Tool for Mac to enable Mac apps to be managed by Microsoft Intune.
Important
The .pkg file must be signed using 'Developer ID Installer' certificate, obtained from an Apple Developer account. Only .pkg files may be used to upload macOS LOB apps to Microsoft Intune. However, conversion of other formats, such as .dmg to .pkg is supported. For more information about converting non-pkg application types, see How to deploy DMG or APP-format apps to Intune-managed Macs.
Download the Intune App Wrapping Tool for Mac.
Note
The Intune App Wrapping Tool for Mac must be run on a macOS machine.
Mark the downloaded tool as an executable:
- Start the terminal app.
- Change the directory to the location where
IntuneAppUtilis located. - Run the following command to make the tool executable:
chmod +x IntuneAppUtil
Use the
IntuneAppUtilcommand within the Intune App Wrapping Tool for Mac to wrap .pkg LOB app file from a .intunemac file.Sample commands to use for the Microsoft Intune App Wrapping Tool for macOS:
Important
Ensure that the argument
<source_file>does not contain spaces before running theIntuneAppUtilcommands.IntuneAppUtil -h
This command will show usage information for the tool.IntuneAppUtil -c <source_file> -o <output_directory_path> [-v]
This command will wrap the .pkg LOB app file provided in<source_file>to a .intunemac file of the same name and place it in the folder pointed to by<output_directory_path>.IntuneAppUtil -r <filename.intunemac> [-v]
This command will extract the detected parameters and version for the created .intunemac file.
Select the app type
- Sign in to the Microsoft Endpoint Manager admin center.
- Select Apps > All apps > Add.
- In the Select app type pane, under the Other app types, select Line-of-business app.
- Click Select. The Add app steps are displayed.
Step 1 - App information
Select the app package file
Microsoft Intune Company Portal
- In the Add app pane, click Select app package file.
- In the App package file pane, select the browse button. Then, select an macOS installation file with the extension .intunemac.The app details will be displayed.
- When you're finished, select OK on the App package file pane to add the app.
Set app information

- In the App information page, add the details for your app. Depending on the app that you chose, some of the values in this pane might be automatically filled in.
- Name: Enter the name of the app as it appears in the company portal. Make sure all app names that you use are unique. If the same app name exists twice, only one of the apps appears in the company portal.
- Description: Enter the description of the app. The description appears in the company portal.
- Publisher: Enter the name of the publisher of the app.
- Minimum Operating System: From the list, choose the minimum operating system version on which the app can be installed. If you assign the app to a device with an earlier operating system, it will not be installed.
- Ignore app version: Select Yes to install the app if the app is not already installed on the device. Select No to only install the app when it is not already installed on the device, or if the deploying app's version number does not match the version that's already installed on the device.
- Install as managed: Select Yes to install the Mac LOB app as a managed app on supported devices (macOS 11 and higher). A macOS LOB app can only be installed as managed when the app distributable contains a single app without any nested packages and installs to the /Applications directory. Managed line-of-business apps will be able to be removed using the uninstall assignment type on supported devices (macOS 11 and higher). In addition, removing the MDM profile removes all managed apps from the device. The default value is No.
- Category: Select one or more of the built-in app categories, or select a category that you created. Categories make it easier for users to find the app when they browse through the company portal.
- Show this as a featured app in the Company Portal: Display the app prominently on the main page of the company portal when users browse for apps.
- Information URL: Optionally, enter the URL of a website that contains information about this app. The URL appears in the company portal.
- Privacy URL: Optionally, enter the URL of a website that contains privacy information for this app. The URL appears in the company portal.
- Developer: Optionally, enter the name of the app developer.
- Owner: Optionally, enter a name for the owner of this app. An example is HR department.
- Notes: Enter any notes that you want to associate with this app.
- Logo: Upload an icon that is associated with the app. This icon is displayed with the app when users browse through the company portal.
- Click Next to display the Scope tags page.
Step 2 - Select scope tags (optional)
You can use scope tags to determine who can see client app information in Intune. For full details about scope tags, see Use role-based access control and scope tags for distributed IT.
- Click Select scope tags to optionally add scope tags for the app.
- Click Next to display the Assignments page.

Step 3 - Assignments
- Select the Required, Available for enrolled devices, or Uninstall group assignments for the app. For more information, see Add groups to organize users and devices and Assign apps to groups with Microsoft Intune.
- Click Next to display the Review + create page.
Step 4 - Review + create
Review the values and settings you entered for the app.
When you are done, click Create to add the app to Intune.
The Overview blade for the line-of-business app is displayed.
The app you have created appears in the apps list where you can assign it to the groups you choose. For help, see How to assign apps to groups.
Note
If the .pkg file contains multiple apps or app installers, then Microsoft Intune will only report that the app is successfully installed when all installed apps are detected on the device.
Update a line-of-business app
Intune Company Portal Mac Download Software
- Sign in to the Microsoft Endpoint Manager admin center.
- Select Apps > All apps.
- Find and select your app from the list of apps.
- Select Properties under Manage from the app pane.
- Select Edit next to App information.
- Click on the listed file next to Select file to update. The App package file pane is displayed.
- Select the folder icon and browse to the location of your updated app file. Select Open. The app information is updated with the package information.
- Verify that App version reflects the updated app package.
Note
For the Intune service to successfully deploy a new .pkg file to the device you must increment the package version and CFBundleVersion string in the packageinfo file in your .pkg package.
Next steps
Intune Company Portal Mac Download Mac
The app you have created is displayed in the apps list. You can now assign it to the groups you choose. For help, see How to assign apps to groups.
Learn more about the ways in which you can monitor the properties and assignment of your app. For more information, see How to monitor app information and assignments.
Learn more about the context of your app in Intune. For more information, see Overview of device and app lifecycles
